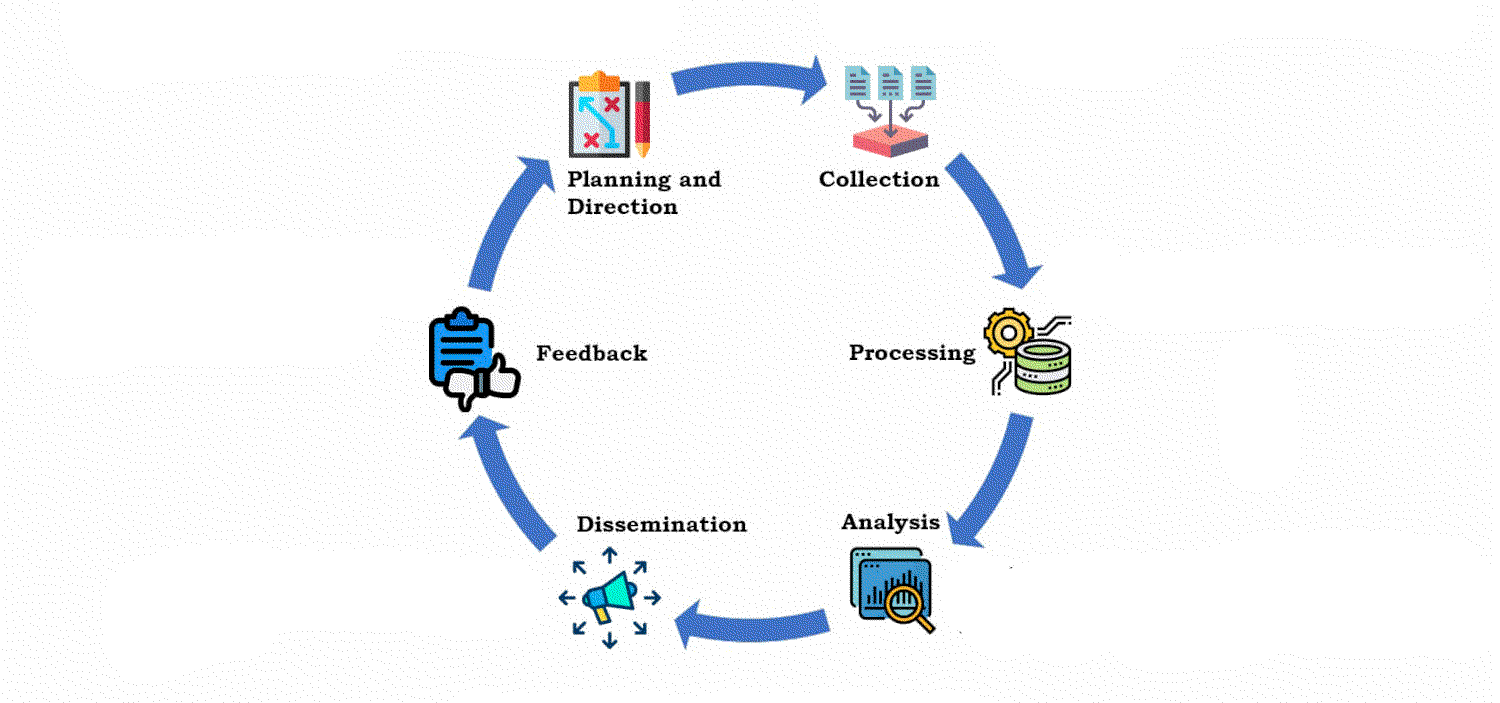
Threat intelligence lifecycle
 |
|---|
| Credits: Introduction to Cyber Threat Intelligence (CTI). |
Threat intel is obtained from a data-churning process that transforms raw data into contextualised and action-oriented insights geared towards triaging security incidents. The transformational process can be expressed in a six-phase cycle:
Direction
Every threat intel program requires to have objectives and goals defined, involving identifying the parameters:
Information assets and business processes that require defending.
Potential impact to be experienced on losing the assets or through process interruptions.
Sources of data and intel to be used towards protection.
Tools and resources that are required to defend the assets.
This phase also allows security analysts to pose questions related to investigating incidents.
Collection
Once objectives have been defined, security analysts will gather the required data to address them. Analysts will do this by using commercial, private and open-source resources available. Due to the volume of data analysts usually face, it is recommended to automate this phase to provide time for triaging incidents.
Processing
Raw logs, vulnerability information, malware and network traffic usually come in different formats and may be disconnected when used to investigate an incident. This phase ensures that the data is extracted, sorted, organised, correlated with appropriate tags and presented visually in a usable and understandable format to the analysts. SIEMs are valuable tools for achieving this and allow quick parsing of data.
Analysis
Once the information aggregation is complete, security analysts must derive insights. Decisions to be made may involve:
Investigating a potential threat through uncovering indicators and attack patterns.
Defining an action plan to avert an attack and defend the infrastructure.
Strengthening security controls or justifying investment for additional resources.
Dissemination
Different organisational stakeholders will consume the intelligence in varying languages and formats. For example, C-suite members will require a concise report covering trends in adversary activities, financial implications and strategic recommendations. At the same time, analysts will more likely inform the technical team about the threat IOCs, adversary TTPs and tactical action plans.
Feedback
The final phase covers the most crucial part, as analysts rely on the responses provided by stakeholders to improve the threat intelligence process and implementation of security controls. Feedback should be regular interaction between teams to keep the lifecycle working.