Command and control phase
The attacker uploaded the file to the server to deface it. While doing so, the attacker used a Dynamic DNS to resolve a malicious IP. The objective in this phase would be to find the IP that the attacker decided the DNS.
To investigate the communication to and from the adversary’s IP addresses, examine the network-centric log sources.
First pick fortigate_utm to review the firewall logs and then move on to the other log sources.
index=botsv1 sourcetype=fortigate_utm"poisonivy-is-coming-for-you-batman.jpeg"
Look at the fields on the left panel and the field url contains the FQDN (Fully Qualified Domain Name).
Verify the answer by looking at another log source.stream:http.
index=botsv1 sourcetype=stream:http dest_ip=23.22.63.114 "poisonivy-is-coming-for-you-batman.jpeg" src_ip=192.168.250.70
Confirm the domain by looking at the last log source stream:dns to see what DNS queries were sent from the webserver
during the infection period.
Questions
This attack used dynamic DNS to resolve to the malicious IP. What fully qualified domain name (FQDN) is associated with this attack?
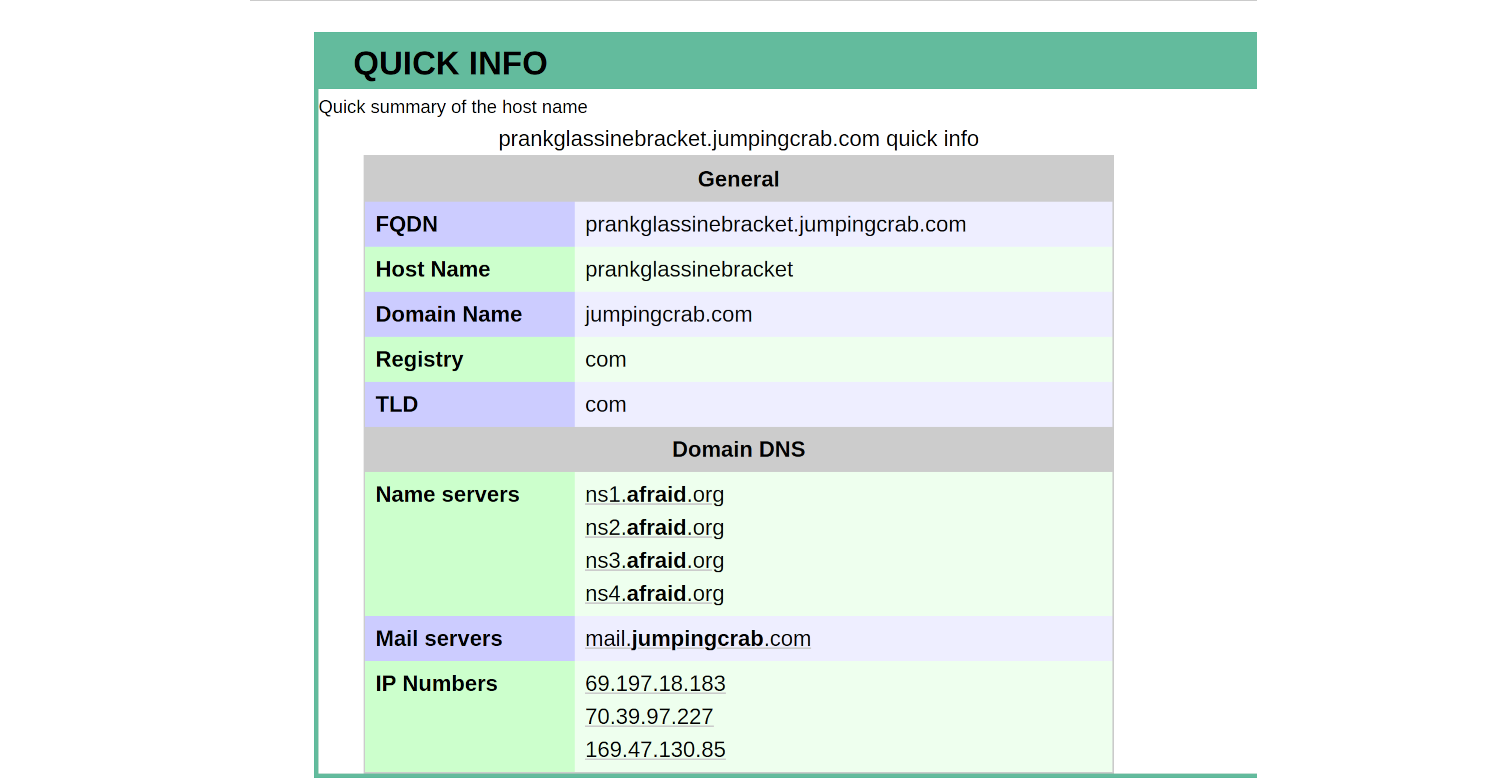 |
|---|
prankglassinebracket.jumpingcrab.com |