Delivery phase
We have identified various IP addresses, domains and Email addresses associated with this adversary.
Attackers create malware and infect devices to gain initial access or evade defenses and find ways to deliver it through different means.
This investigation phase would be to use the information we have about the adversary and use various Threat Hunting platforms and OSINT sites to find any malware linked with the adversary.
Threat Intel report suggested that this adversary group Poison lvy appears to have a secondary attack vector in case the initial compromise fails. Our objective would be to understand more about the attacker and their methodology and correlate the information found in the logs with various threat Intel sources.
OSINT sites
Questions
What is the HASH of the Malware associated with the APT group?
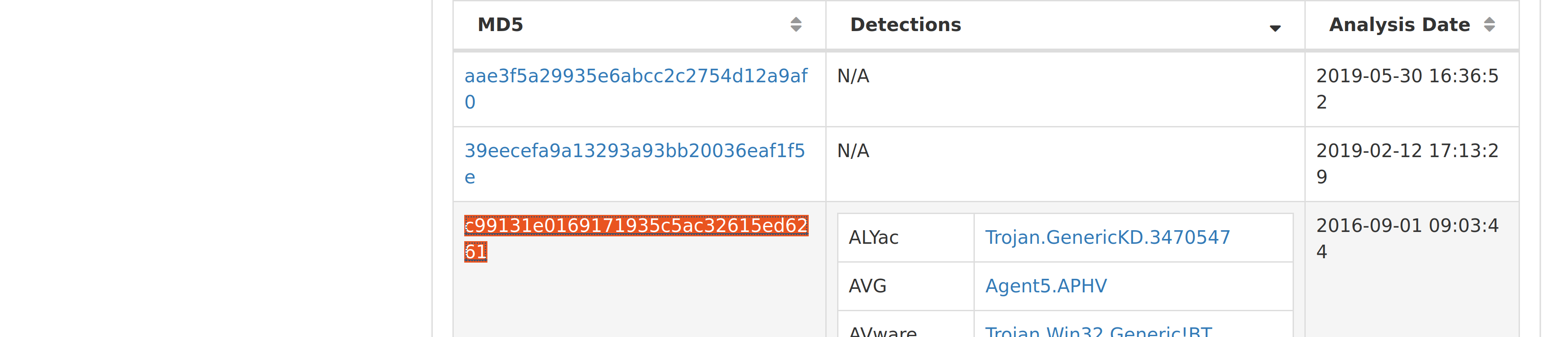 |
|---|
c99131e0169171935c5ac32615ed6261 |
What is the name of the Malware associated with the Poison Ivy Infrastructure?
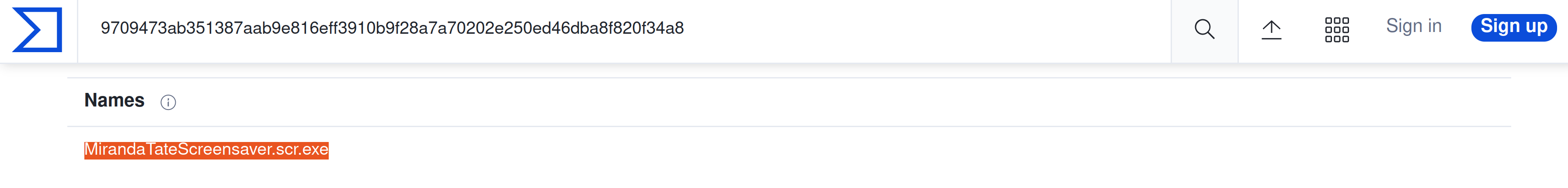 |
|---|
MirandaTateScreensaver.scr.exe |